Restrict full-scoped personal access token creation in Azure DevOps
Right now a PAT (Personal Access Token) can be created for all the scopes like Work items, Repositories, Build and release pipelines which literally gives unrestricted access to any PAT token created with all the scopes. But from security perspective this is a very bad practice. So as to restrict this, Azure DevOps provides an feature which allows a organization admin to restrict that no full scoped PATs should be created. This would enable greater security because even if the PAT token is leaked, it would not have access to all the scopes. Let us see what are the steps to restrict full scoped personal access token creation in Azure DevOps
Prerequisites: User should have been assigned Azure DevOps Admin role in Azure Active Directory and should be a Project Collection Administrator
Step 1: Go to Organization Settings
Step 2: Click on Azure Active Directory
Step 3: Scroll to the section “Restrict full-scoped personal access token creation”
Step 4: Enable the option to restrict full scoped personal access token creation. Once this option is enabled, users wont be able to create PATs including all the scopes. They would be able to create only including the scopes they need,
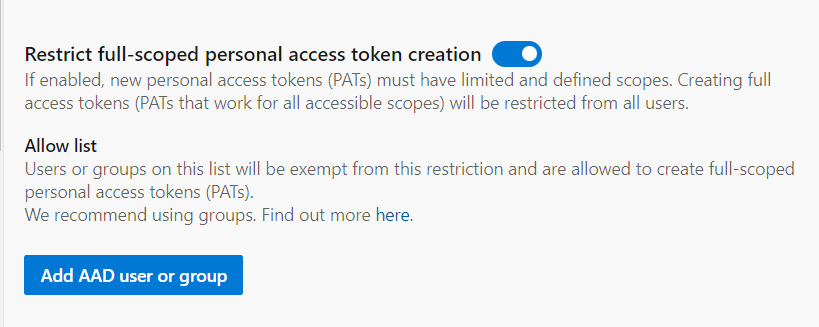
Step 5: Incase if someone users need to have access to create PATs with all the scopes then they can be added in the exception list known as allowed list. Users part of the allow list would be able to create PATs with all the scopes.
